Using one security token (a username and password pair), user access can be enabled and disabled for multiple systems, platforms, apps and other resources. This reduces the risk of lost, forgotten or weak passwords.
Single sign-on (SSO) is a centralized session and user authentication service in which one set of login credentials can be used to access multiple applications. SSO can be great for productivity, IT monitoring and management and security control.
SSO can be used from the login page or to bypass the login page, and from another page or system.
The Cloudmore platform supports Single Sign-On (SSO) using SAML 2.0 protocol, allowing Cloud Broker administrators to log into Cloudmore using the authentication protocol in their own system. Once authenticated, the user does not need to re-enter details to log into Cloudmore.
Configuration for Cloud Service Brokers
Please follow these steps to set up SSO:
1. The Cloud Broker needs to have an Identity Provider (IdP) system working to support the SAML 2.0 protocol.
2. The Cloud Broker can then input their IdP system’s metadata in Cloudmore.
3. Cloudmore will provide the Cloud Broker with ‘Service Provider’ metadata to input in the IdP system.
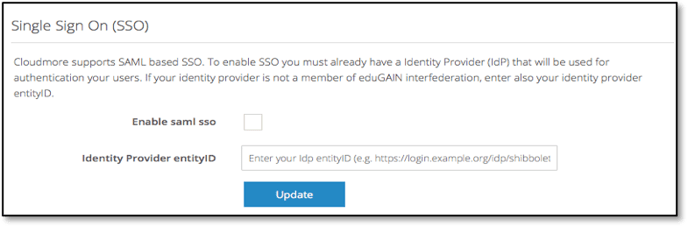
4. The SSO feature needs to be enabled in the Cloudmore Security Center.
4.1 ‘Enable SAML SSO’.
4.2 Enter the Identity Provider (IdP) URL in the ‘Identity Provider EntityID’ field. This URL is used to redirect users to the IdP system where the authentication happens.
5. To use SSO, administrators must have an existing user account in Cloudmore. This account is used to match the federated user with a Cloudmore account that will also determine user access and rights within Cloudmore. No accounts are created automatically during login for security reasons.
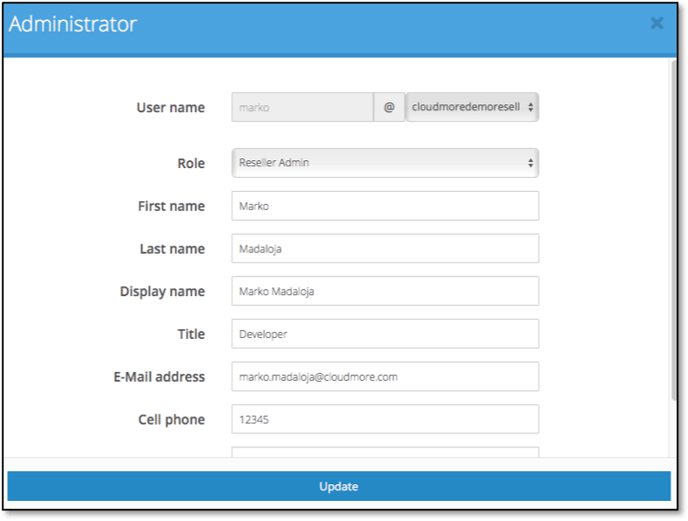
6. The federated user will be matched to a Cloudmore account through the “mail” attribute. This attribute should be a unique attribute and must be returned with the authentication response from the IdP.
7. For example, if the user in the customer’s system has a username (or email) such as; name@company.samlidp.io, then the user created in the reseller/admin.aspx page must be the same, or be easily identified as related/connected. See below.
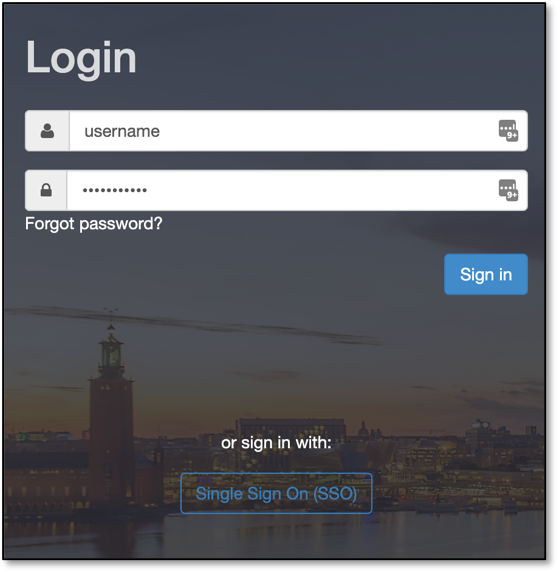
8. Once the configuration is complete, a user can initiate the SSO authentication on their login page using the ‘Single Sign-On (SSO)’ option.
Automatic Login
For instance, if you want to automate the login process and trigger SSO authentication from a different system, you can specify the Identity Provider (IdP) in the URL. This method allows the user to bypass the normal login page completely and, if already authenticated, access Cloudmore directly.
You need to have SSO setup and working. Use the below URL and update the "<Branded_URL>" with the URL you use to access Cloudmore, and replace the "<URL_to_the_IdP>" with the URL to your Identity Provider.
https://<Branded_URL>/Shibboleth.sso/Login?entityID=<URL_to_the_IdP>
Example: https://www.brokerdomain.com/Shibboleth.sso/Login?entityID=https://sts.windows.net/00000000-0000-0000-0000-000000
END
