DAP vs GDAP
The Delegated Admin Privileges (DAP) is a Microsoft security framework that allows a Microsoft partner to access and carry out day-to-day operations on behalf of their customers. These operations are, for instance, creating users and assigning licenses.
The DAP framework assigns the Global Admin role to the Microsoft Partner; therefore, the partner has full access to the customer tenant. From a security point-of-view, this makes it vulnerable to supply chain attacks and other risks.
To address this, Microsoft has released an updated version of DAP called Granular Delegated Admin Privileges (GDAP). GDAP allows for more granular and time-bound access from the partner to their customer tenants. This least-privileged access needs to be explicitly granted to partners by their customers.
GDAP is already launched and will fully replace DAP on January 17, 2023.
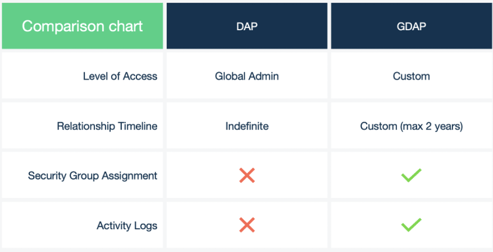
GDAP allows partners access to their customer tenants in a more granular-level time-bounded access, while giving customers additional control on what partners can access.
-
Partners can select GDAP relationship duration from 1 day to 730 days.
-
Partners choose the requested granular level roles (not recommended to select “Global Admin”). The least privileged role should be used.
-
A GDAP relationship is established by a Partner who sends a request to a customer, and the customer needs to approve the request. The request needs to be created from Partner Center. The customer needs to have a Global Admin role to approve the request.
-
A GDAP relationship is, by default, for two years. The partner can specify shorter time frames ranging from 1 day to 2 years.
-
Partners can create security groups to organize their team member access to customer tenants with separate roles.
-
Partners can use GDAP reporting analytics to track expiring relationships.
-
Customers can track partners' activity logs in Azure AD Sign-in Logs.
-
A GDAP relationship will not auto-renew. Instead, the partner needs to send a new GDAP request to the customer, and the customer needs to approve it again.
-
GDAP affects both Microsoft Partner Center and the Partner Center APIs that Cloudmore uses. Therefore, the GDAP restrictions will apply to both Partner Center and Cloudmore. If you don’t have permission to create users in Partner Center, you can’t create users through Cloudmore either.
How to request a GDAP relationship
GDAP relationships cannot be managed in Cloudmore. Instead, the partner needs to configure GDAP in Microsoft Partner Center.
Detailed instructions from Microsoft can be found here: https://docs.microsoft.com/en-us/partner-center/gdap-obtain-admin-permissions-to-manage-customer
Assign security groups
It is not enough to only request GDAP permissions. After the permissions have been accepted, the partner needs to assign the permissions to the AdminAgent security group.
Detailed instructions from Microsoft can be found here: Grant granular permissions to security groups - Partner Center.
Least Privilege Permissions
Microsoft has defined the least privileged role required to carry out a task. These permissions apply to both Microsoft Partner Center and Cloudmore.
For information on least privilege roles, please see: GDAP role guidance - Partner Center
Cloudmore requires three roles in each organization to fully function: Directory Readers, User Administrators, and License Administrators.
|
Task in Cloudmore |
Role |
Why needed |
|---|---|---|
|
Manage Users |
User Administrator Directory Readers |
The User Administrator role is needed to create, view and edit Microsoft users in Cloudmore. The Directory Readers is needed to create new users as Cloudmore need to read organization properties to create the user. |
|
Manage Licenses |
License Administrator Directory Readers |
The License Administrator is needed to assign and revoke licenses from users. The Directory Readers is needed to view licenses in Cloudmore. |
Cloudmore recommends having one of the following roles in addition to the least privilege roles above to ensure that the Cloudmore CPV application has consent granted through automation in the customer's tenant. Application consent is the process of a resource owner granting authorization for a client application to access protected resources, under specific permissions, on behalf of the resource owner. Cloudmore closely follows the Microsoft security guidelines and requires explicit app + user consent for every customer tenant.
|
Task in Cloudmore |
Role |
Why needed |
|---|---|---|
|
Grant Application Consent |
Application Administrator (replaced Privileged Role Administrator) or Cloud Application Administrator |
The Application Administrator role is needed to create and manage all aspects for giving consent and using the Cloudmore app. |
For information on application consent, please see: GDAP and secure application model - Partner Center
Features that do not require permissions
As long as the Microsoft partner has a Partner Relationship with the customer, these features do not require any GDAP roles for both the Microsoft 365 and Azure products:
-
Subscription management
-
Price management
-
Link Tenants
-
MCA management
-
Cost center management
What happens if a role is missing?
If a GDAP role is missing, those tasks cannot be carried out in either Partner Center or Cloudmore. For instance, if the User Administrator role has not been given, no user accounts can be viewed, created, or deleted for the customer either through Partner Center or Cloudmore. Cloudmore will function without the role, but the user and license views will be empty.
Trouble-shoot GDAP permissions
Log in to Partner Center and navigate to the customer and then click on Admin relationships. Make sure you have one (do not split into several admin requests) admin relationship with the User Administrator, License Administrator, and Directory Readers role. Make sure the admin relationship has a status of Active. Click on the Admin relationship and make sure you have added the AdminAgents to the security groups of the admin relationship and assigned all three permissions to the group.
Please ensure that the account used to integrate your CSP tenant with Cloudmore is added to any existing security groups used for the current Admin relationship(s).
Sometimes customer information might not propagate to Cloudmore after transition to GDAP, even though it is available in the Microsoft Partner Center. It means you have to refresh Azure app registration info in order to fetch a new list of permissions. You can do it by updating your authentication token on the Microsoft 365 CSP Direct - Microsoft CSP Authentication page in Cloudmore.
